Vulnerability Assessment & Penetration Testing (VAPT)
About Us
In today’s rapidly evolving digital landscape, cybersecurity threats are more sophisticated and persistent than ever. Attackers are constantly probing for weaknesses in systems, applications, networks, and devices—making it critical for businesses to adopt a proactive approach to security.
At Datanet Hosting Solutions Pvt. Ltd., we offer end-to-end Vulnerability Assessment and Penetration Testing (VAPT) services that help organizations identify, evaluate, and mitigate potential security risks before malicious actors exploit them. Whether you’re a startup, SME, or enterprise, our goal is to empower you with real-world insights into your security posture so you can defend against evolving cyber threats.
Our approach goes far beyond automated vulnerability scanning. We combine automated tools with manual penetration testing techniques to simulate real-world cyberattacks. This allows us to not only detect known vulnerabilities but also identify zero-day exploits, business logic flaws, and misconfigurations that automated tools might miss.
Every VAPT engagement is tailored to your organization’s environment—be it on-premise, cloud-based, or hybrid—and aligned with leading standards like OWASP, NIST, ISO 27001, and PCI-DSS.
VAPT Services We Offer
Why Your Business Needs VAPT?:-
-
Stay One Step Ahead of Hackers: VAPT helps uncover vulnerabilities before attackers do.
-
Meet Compliance Requirements: Required for regulatory standards like PCI-DSS, GDPR, HIPAA, and ISO 27001.
-
Protect Business Continuity: A security breach can lead to downtime, financial losses, and reputational damage.
-
Enhance Customer Trust: Proving your systems are secure builds confidence with clients and stakeholders.
-
Tailored Risk Management: Every organization has unique security challenges—we provide custom strategies to mitigate them.
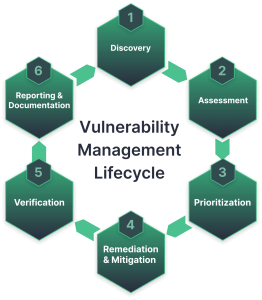
Network Vulnerability Assessment:-
We assess both internal and external networks to uncover weaknesses like unpatched systems, misconfigurations, open ports, insecure protocols, and unauthorized access points.
Key Highlights:
-
-
Firewall, router & switch analysis
-
Network segmentation review
-
Detection of exploitable services
-
Risk-based vulnerability classification
-

Web Application Penetration Testing:-
Our experts simulate attacks on your web applications to detect critical flaws, such as injection vulnerabilities, authentication bypass, session hijacking, and insecure APIs.
Key Highlights:
-
OWASP Top 10 coverage
-
Manual + automated testing
-
Input validation & session management checks
-
Secure code validation (optional)
Mobile App Security Testing:-
We test Android and iOS apps for both client-side and server-side vulnerabilities, ensuring secure data handling, encryption, and communication.
Key Highlights:
- Static & dynamic analysis
- Jailbreak/root detection bypass tests
- SSL/TLS implementation validation
- Reverse engineering and local storage review
-

Cloud Infrastructure Security Testing:-
Our cloud VAPT focuses on identifying misconfigurations, excessive permissions, and data exposure in cloud platforms like AWS, Azure, and Google Cloud.
Key Highlights:
- IAM policy evaluation
- Security group and ACL checks
- Cloud storage exposure analysis
- Container & serverless security
Internal & External Penetration Testing:-
We simulate both insider and outsider threats to test the strength of your overall IT infrastructure and understand how far an attacker could go once access is gained.
Key Highlights:
-
Exploitation of real vulnerabilities
-
Lateral movement testing
-
Privilege escalation analysis
-
Post-exploitation impact reporting
-

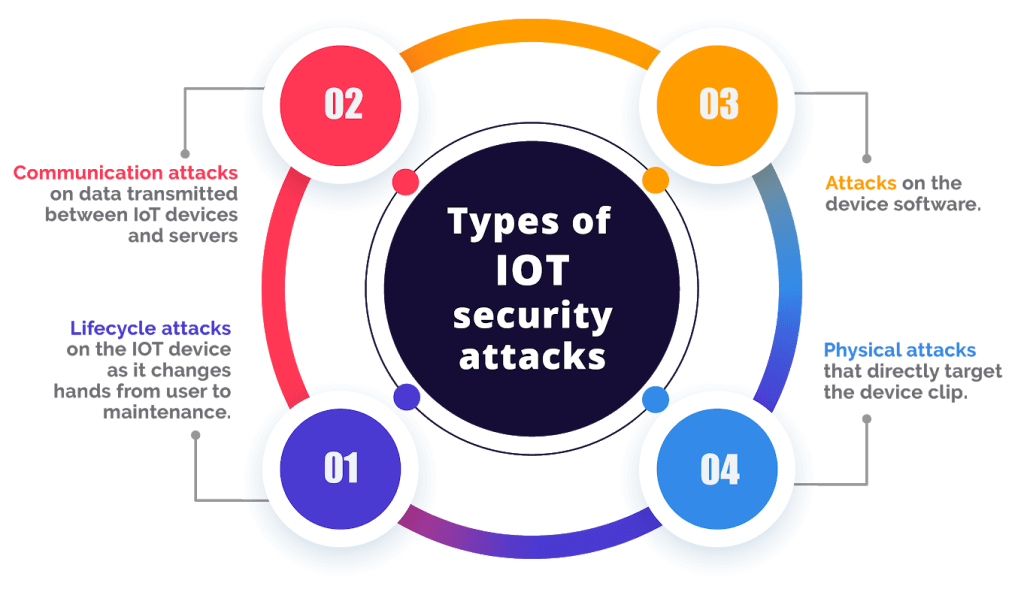
IoT & API Security Testing:-
IoT devices and APIs are often overlooked but critically vulnerable. Our testing ensures your smart devices and application interfaces are secure by design.
Key Highlights:
-
Firmware and configuration review
-
API endpoint testing (authorization, rate limiting, fuzzing)
-
Device-to-server communication analysis
-
Protocol-level security testing (MQTT, CoAP, etc.)
FAQs: Everything You Need to Know
Vulnerability Assessment identifies known security weaknesses using automated tools, while Penetration Testing goes a step further by actively exploiting vulnerabilities to simulate real-world attacks.
VAPT should be conducted at least once a year or after major infrastructure or application changes, product releases, or regulatory updates.
We offer non-intrusive testing during business hours and intrusive testing during maintenance windows to ensure minimal disruption.
Yes, we deliver detailed reports aligned with compliance standards like ISO 27001, PCI-DSS, HIPAA, and GDPR, including risk severity, exploitation details, and remediation steps.
VAPT is essential for businesses of all sizes. Startups benefit greatly as early detection of vulnerabilities helps avoid costly breaches and builds customer trust.
Yes. Our AI chatbots support multi-language communication, helping you connect with global users and offer localized experiences—improving both engagement and conversion.
The duration depends on the scope and complexity of the environment. On average, a standard VAPT project may take 5 to 10 business days, including assessment, exploitation, reporting, and review sessions.
Yes, we provide detailed remediation guidance in our reports and offer consulting support to help your IT or development teams patch the identified vulnerabilities effectively.
Absolutely. Our team comprises certified professionals including CEH, OSCP, CISSP, and CREST-certified testers with deep expertise in real-world threat modeling and exploitation.
Most VAPT services can be delivered remotely and securely, especially for external testing. For internal network assessments, an on-site presence may be required depending on your infrastructure and security policies.







